The Office of Information Technology has recently launched a campaign to increase Information Security awareness at the College of Charleston.
What is Phishing?
Phishing is fraud perpetrated on the Internet. To phish is to trick a person into revealing personal information. It is also defined as perpetrating online fraud by impersonating a company or person:
phishing, n.
Fraud perpetrated on the Internet; the impersonation of reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers, online.
phish, v.
To perpetrate a fraud on the Internet in order to glean personal information from individuals, especially by impersonating a reputable company; to engage in online fraud by deceptively ‘angling’ for personal information.
Typically, phishers send emails under false pretenses. They pose as authoritative sources such as PayPal, eBay, Helpdesk, and System Administrators. Messages include warnings about account statuses and ask users to reply, update, validate, or confirm private information.
How can you avoid the phishing trick? The first step is identification. Phishing may not be obvious in the sender’s name or email address. Before proceeding with any requests, what exactly is the message asking you to do? If you receive an unsolicited request for information such as username or password, you have phishing. If you suspect phishing, do not respond. Simply delete the email.
Remember, no department or person at the College of Charleston will ever request your username or password by email or phone.
The Office of Information Technology has set-up a Phishing IQ Test. It is intended to test your ability to identify phishing scams.
The Risk of Phishing
Due to the amount of email users, the College is frequently a target of phishing attacks. If a single community member responds to a fraudulent email, the perpetrator has the potential to launch more attacks from the infiltrated account. Recently, a compromised account sent out approximately 200,000 email messages. One response causes a domino effect of increased risk. The flood of emails not only increases risk, it also impedes the College’s email service.
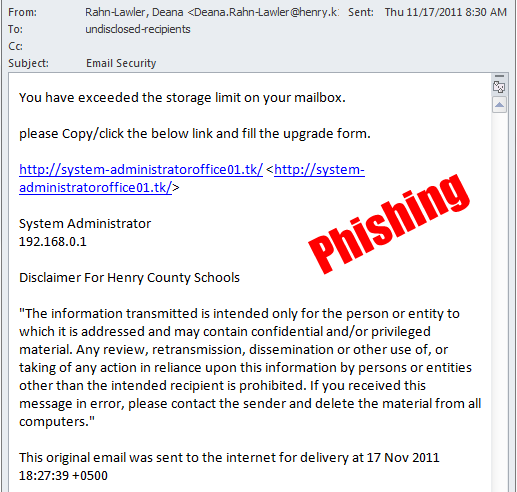
What does Phishing Look Like?
Above is one example of phishing. More examples are available for viewing on the Information Security web page.
The best way to guard against phishing is to stay informed. Be sure to protect yourself and others!